In organizations where multiple users access the same data, ensuring that sensitive information is only visible to authorized personnel is crucial. Without proper controls, there’s a risk of unauthorized data exposure, leading to compliance issues and inefficiencies.
Business Central offers robust security controls out of the box, including the ability to manage access at the table and page level using permission sets and security filters. While native field-level security such as restricting access to individual fields within a record is currently unavailable, organizations can still achieve this level of granularity through third-party extensions or custom development. With the right configuration, Business Central can be adapted to meet specific data privacy and compliance needs.
Business Central’s Field-Level Security Capabilities and Limitations
Field-level security refers to the ability to control user access to individual data fields within a record. It allows administrators to specify exactly which fields a user can view or edit, helping organizations protect sensitive data and support compliance needs.
In Microsoft Dynamics 365 Business Central, permissions can be configured to control access at the table and page level, allowing administrators to define what a user can read, insert, modify, or delete. For example, you could prevent a junior HR assistant from opening the Employee Card page, or restrict a sales rep from accessing the Sales Price table that contains sensitive margin data.
While you can’t hide or disable individual fields out of the box, you can restrict access to the full pages or tables where those fields reside. This helps maintain a basic level of confidentiality without needing custom development or third-party solutions.
To achieve more granular control, organizations typically turn to third-party extensions. One such extension is Advanced Cloud Security, which enables true field-level security in Business Central. This app allows administrators to hide or restrict access to individual fields based on user roles — without requiring custom development. As your organization scales and roles become more specialized, implementing field-level access can improve data governance and ensure that employees only access the information they truly need.

Why Does Field-Level Security Matter in Business Central?
One of the most common oversights is not fully leveraging permission sets and user groups, which allow administrators to restrict access to entire tables or pages based on role. Without clearly defined access levels, users may unintentionally view or modify information beyond their scope of responsibility, increasing the risk of errors or internal data leaks.
Sensitive data visibility is another concern. Business Central allows administrators to design role-based permissions that control access to full tables or specific pages. When these are not used effectively, users may be granted broader access than necessary, exposing confidential business or employee data.
For organizations in regulated industries, failing to control data access can lead to compliance violations and potential penalties. Business Central’s native security model, when properly configured, supports audit readiness by tracking user permissions and restricting access in alignment with governance standards.
Not utilizing Business Central’s built-in tools also increases the likelihood of workflow disruptions. When users have access to too much or too little information, it can impact productivity and create unnecessary confusion. Without clear boundaries in place, users may end up accessing irrelevant or sensitive information, leading to inefficiencies.
How Do You Configure Field-Level Security in Business Central?
Business Central includes powerful out-of-the-box capabilities for managing data access at the table and page level. These settings allow administrators to define exactly what users can view, edit, or delete. Here’s how to configure it effectively:
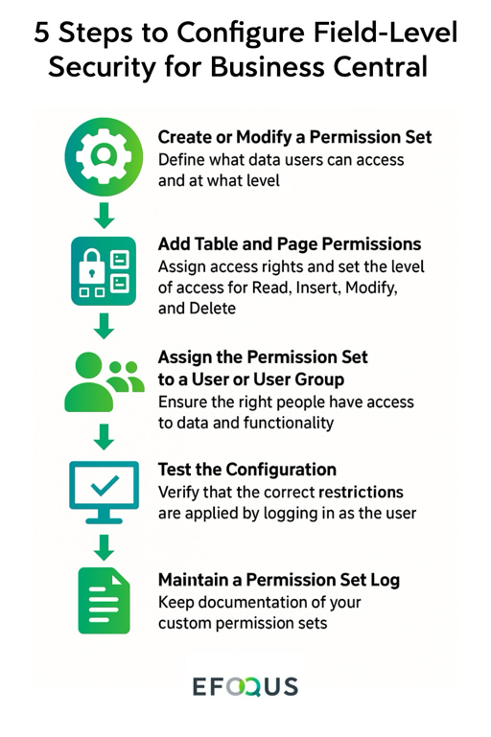
1. Create or Modify a Permission Set:
Start by navigating to Permission Sets in Business Central. You’ll find this under the Users section in the Microsoft 365 Admin Center or directly through the Permissions page in the User Setup area of the application. This is where you define what data users can access and at what level. You can either create a new permission set from scratch or duplicate an existing one and modify it. Duplicating system-defined sets is often a good starting point, as it allows you to build on standard configurations without altering core defaults.
2. Add Table and Page Permissions:
Within the permission set, assign access rights by specifying the Object Type (Table or Page) and the Object ID. From there, you can set the level of access for Read, Insert, Modify, and Delete.
3. Assign the Permission Set to a User or User Group:
Once your permission set is configured, assign it to specific users or user groups. This ensures that only the right people have access to the designated data and functionality.
4.Test the Configuration:
Before rolling it out broadly, log in as the user (or use the Effective Permissions feature) to verify that the correct restrictions are applied. This helps catch any unintentional gaps and ensures the user experience remains smooth.
5. Maintain a Permission Set Log:
Keep documentation of your custom permission sets, including what each one is for, which objects it modifies, and who it’s assigned to. This helps streamline audits and makes it easier to scale or troubleshoot later.
Managing Long-Term Business Central Security
Field-level security requires ongoing attention as your organization evolves. Teams change, roles shift, and new data is added, which makes it essential to regularly review who has access to what. Scheduling access reviews quarterly or after any major organizational changes helps ensure your permissions remain aligned with current responsibilities and minimizes the risk of overexposure.
To keep your field-level security effective and sustainable over time, consider these best practices:
- Review permissions quarterly to verify they match your organizational structure.
- Audit access after role or team changes to quickly address any gaps or outdated access.
- Keep permission documentation up to date so changes are clearly tracked and easy to maintain.
- Use extensions with audit trails and reporting to monitor access and support internal reviews or compliance checks. Advanced Cloud Security, for example. includes built-in audit capabilities, making it easier to track field-level access and maintain compliance over time.
Business Central Field-Level Security FAQs
1. Can I restrict access to individual fields in Business Central?
Answer:
Out of the box, Microsoft Dynamics 365 Business Central does not support true field-level security. You can restrict access at the table or page level using permission sets, but not to specific fields within a record. However, third-party extensions or custom development can be used to achieve field-level restrictions, such as hiding or disabling individual fields based on user roles.
2. How do I set up security to protect sensitive data in Business Central?
Answer:
To secure data, start by creating or modifying permission sets that define user access at the table or page level. Assign these to users or user groups, specifying what they can read, insert, modify, or delete. Then, test the configuration and maintain a log of your permission sets for audit readiness and easier maintenance.
3. What are best practices for managing field-level security over time?
Answer:
Managing field-level security is an ongoing process. Best practices include:
- Quarterly reviews of permissions to ensure alignment with current roles.
- Immediate audits after team or role changes.
- Keeping documentation of permission sets up to date.
- Using extensions with audit trails to monitor access and support compliance.
Securely Set Up Business Central with EFOQUS
Field-level security is essential for businesses that want to protect sensitive information. With the right setup and ongoing oversight, Business Central can become a secure, role-appropriate workspace for every team member.
EFOQUS helps organizations take full control of their Business Central environment, ensuring the right people have the right access. From initial setup to ongoing optimization, we help you safeguard sensitive data without disrupting your workflows. Take the next step and partner with EFOQUS.